Now that you’re all set, it’s time to learn the basics. AdGuard Home offers you a rich framework to work with, and it’s up to you which way you’ll decide to go. To help you kick things off, here’s a quick rundown on AdGuard Home features.
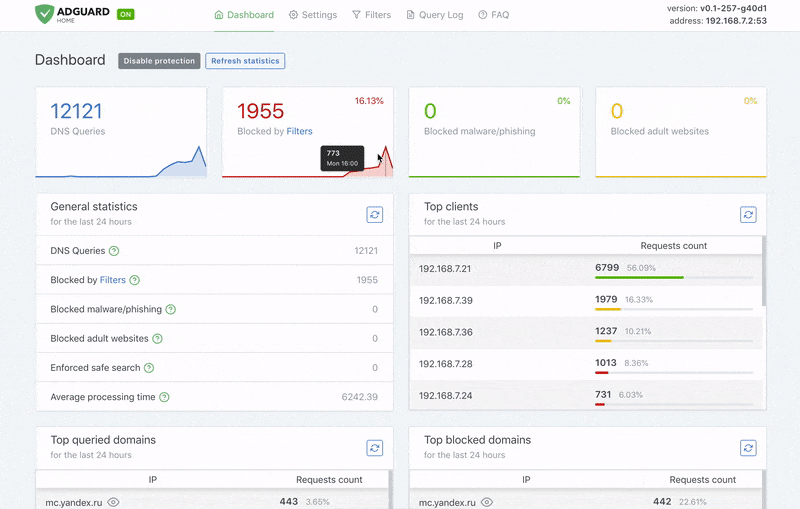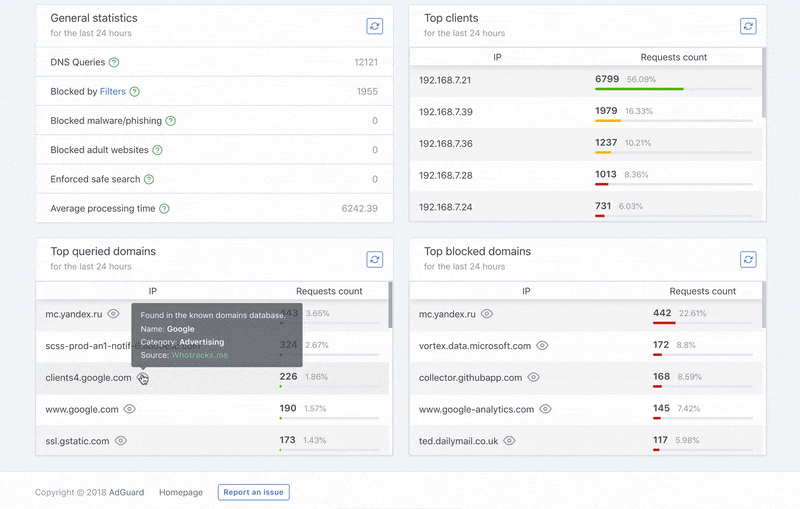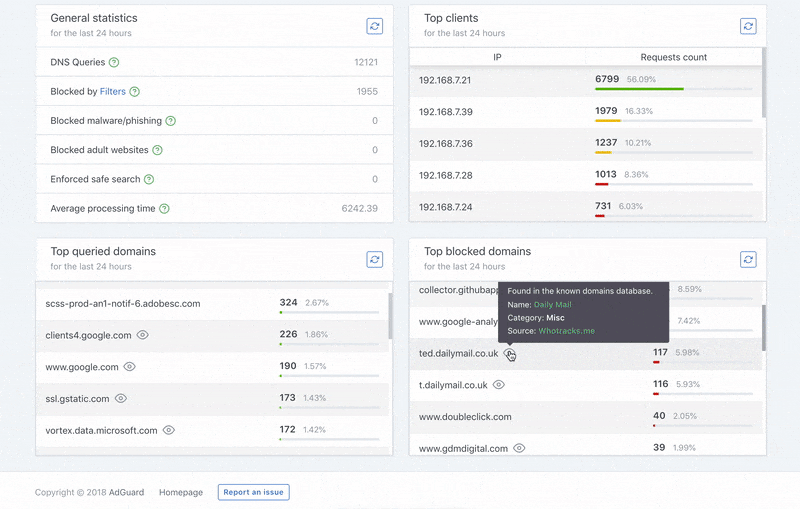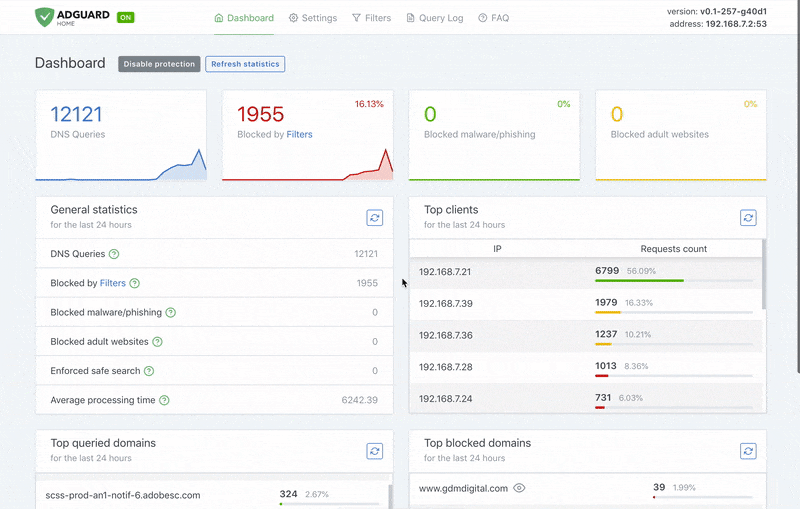
This is your dashboard, the information hub that you can use to learn about all activities happening at AdGuard Home. You can’t do much directly from this screen, only see the general picture, but it’s a good starting point to move on to other settings.
All changes you make here will be automatically applied to all devices connected to AdGuard Home, unless specified otherwise.
AdGuard Home is a blocking DNS server at its core, and this is the place to configure everything DNS-related: upstreams, bootstraps, cache, access settings etc.
You’ll find this useful if you want your admin interface to work via HTTPS and your DNS server to listen for requests over DNS-over-HTTPS and DNS-over-TLS.
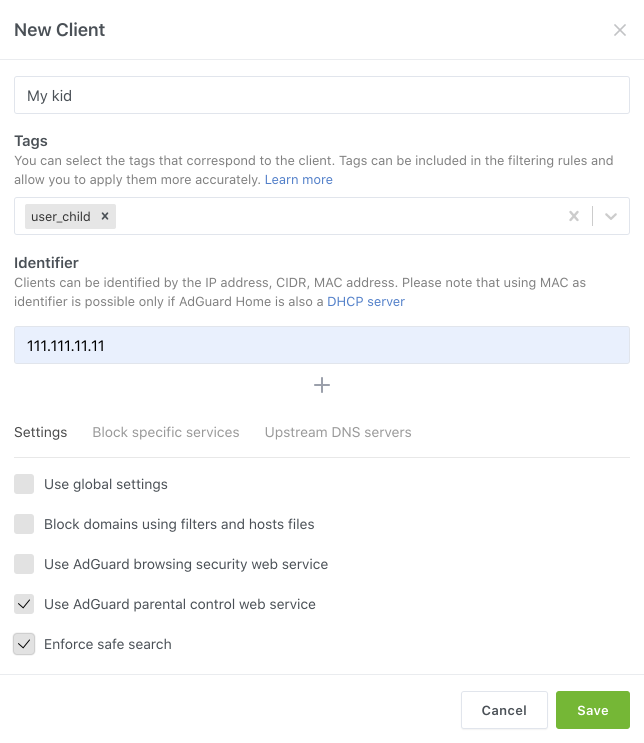
Here you can add your devices as clients (by IP, MAC address or CIDR) and set specific permissions for them. For example, disable TikTok for your work laptop or enforce safe search for your kids’ tablets.
On DHCP settings tab you can setup AdGuard Home as your own built-in DHCP server. This makes configuring the Clients much easier as it allows to distinguish them by their MAC addresses.
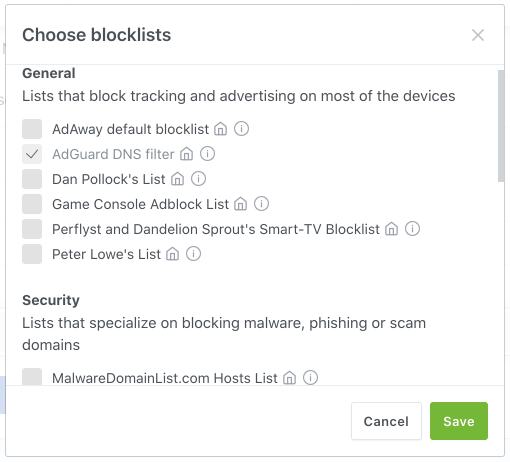
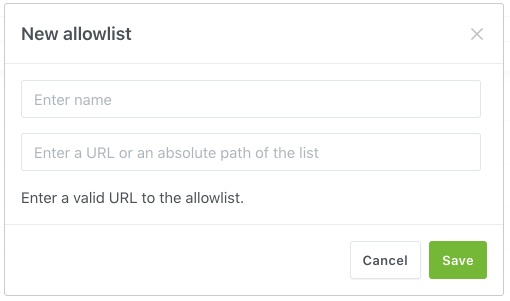
Add DNS blocking lists to block access to ad, tracking and malware domains. AdGuard supports basic adblock rules or hosts files syntax. Lists added to “DNS allowlists” section will unblock domains instead.
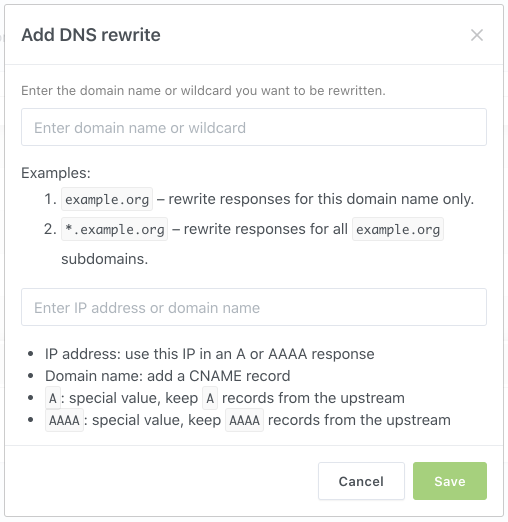
“Rewrites” tab allows you to redirect specific DNS requests (say, requests to example.org and its subdomains) to a specific domain or IP address.
One-click way to block access to some of the popular services like Facebook or Twitter. Note that these changes will be applied to all clients by default.
Custom filtering rules. This is the place to fine-tune your filtering. Custom rules support the same syntax as DNS blocklists but can be added individually and not as a part of a larger list.
Query log contains detailed information on all processed DNS requests inside your network. For known trackers AdGuard Home will display additional details.















